diff --git a/docs/SUMMARY.md b/docs/SUMMARY.md
index ac0633fab..ccb72d294 100644
--- a/docs/SUMMARY.md
+++ b/docs/SUMMARY.md
@@ -185,7 +185,7 @@
* [Connect SpringBoot with Mysql Database](user-guide/use-cases/connect-springboot-with-mysql-database.md)
* [Connect Expressjs With Mongodb Database](user-guide/use-cases/connect-expressjs-with-mongodb-database.md)
* [Connect Django With Mysql Database](user-guide/use-cases/connect-django-with-mysql-database.md)
- * [Pull Helm Charts from OCI Registry](user-guide/use-cases/oci-pull.md)
+ * [Deploying Software on Air-gapped Environment](../docs/user-guide/use-cases/airgapped-app-deployment.md)
* [Telemetry Overview](user-guide/telemetry.md)
* [Devtron on Graviton](reference/graviton.md)
* [Release Notes](https://github.com/devtron-labs/devtron/releases)
diff --git a/docs/user-guide/creating-application/workflow/cd-pipeline.md b/docs/user-guide/creating-application/workflow/cd-pipeline.md
index 11b84d1e0..dabc51265 100644
--- a/docs/user-guide/creating-application/workflow/cd-pipeline.md
+++ b/docs/user-guide/creating-application/workflow/cd-pipeline.md
@@ -32,7 +32,7 @@ This section expects four inputs from you:
| Setting | Description | Options |
| ----------- | ---------------------------------------------------------- | ------------------------- |
-| Environment | Select the environment where you want to deploy your application | (List of available environments) |
+| Environment | Select the environment where you want to deploy your application. | (List of available environments) |
| Namespace | Automatically populated based on the selected environment | Not Applicable |
| Trigger | When to execute the deployment pipeline | **Automatic**: Deployment triggers automatically when a new image completes the previous stage (build pipeline or another deployment pipeline)
**Manual**: Deployment is not initiated automatically. You can trigger deployment with a desired image. |
| Deployment Approach | How to deploy the application | **Helm** or **GitOps**
Refer [GitOps](../../global-configurations/gitops.md) |
@@ -44,7 +44,7 @@ This section expects four inputs from you:
In case you are choosing an [isolated environment](../../global-configurations/cluster-and-environments.md#add-isolated-cluster) for deployment, you will get two additional options to choose from in the 'Deploy to Environment' window ([check snapshot](https://devtron-public-asset.s3.us-east-2.amazonaws.com/images/use-cases/oci-push/create-cd2.jpg)):
* **Do not push** - A link to download the helm package will be available after the deployment. However, it will not push the helm package to the OCI registry.
* **Push to registry** - This will generate and [push the helm package to the OCI registry](../../global-configurations/container-registries.md#push-helm-packages). Upon selecting this option, you will get two more fields:
- * **Registry** - Choose the OCI registry to which the helm chart package must be pushed. Only those registries that have `Push helm packages` enabled will be shown in the dropdown.
+ * **Registry** - Choose the OCI registry to which the helm chart package must be pushed. Only those registries that have [Push helm packages](../../global-configurations/container-registries.md#push-helm-packages) enabled will be shown in the dropdownChoose the OCI registry to which the helm chart package must be pushed. Only those registries that have [Push helm packages](../../global-configurations/container-registries.md#push-helm-packages) enabled will be shown in the dropdown.
* **Repository** - Enter the repository name. You can find the username from your registry provider account (e.g., Docker Hub).
{% endhint %}
diff --git a/docs/user-guide/global-configurations/cluster-and-environments.md b/docs/user-guide/global-configurations/cluster-and-environments.md
index 01e2270b3..e73c4b811 100644
--- a/docs/user-guide/global-configurations/cluster-and-environments.md
+++ b/docs/user-guide/global-configurations/cluster-and-environments.md
@@ -104,6 +104,13 @@ To assign a category to a cluster, follow the steps below:
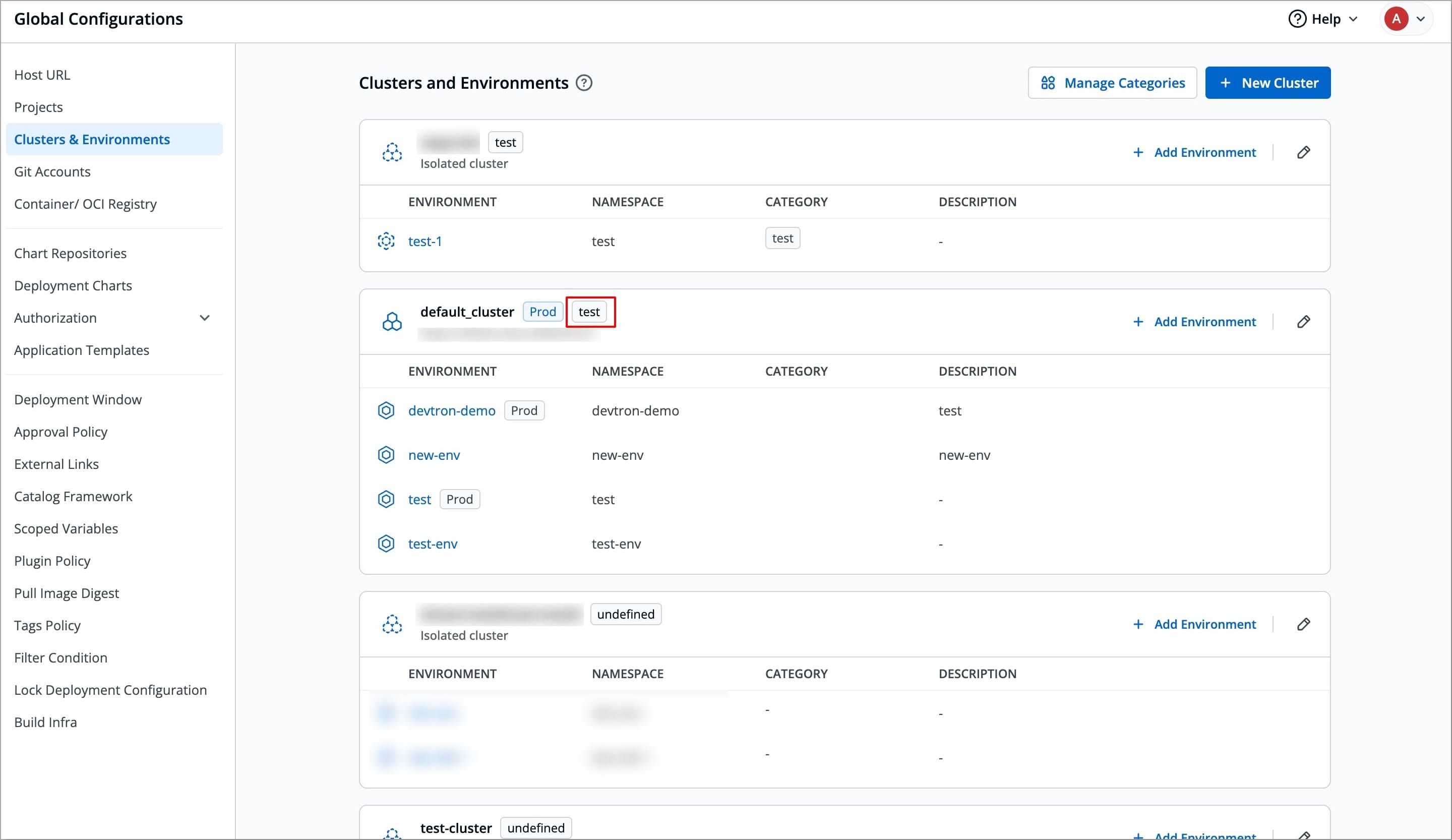
+{% hint style="info" %}
+
+### Note
+
+Refer [Get Cluster Credentials](#get-cluster-credentials) to know the process of getting Server URL and bearer token.
+
+{% endhint %}
### Choose Method of Connection [](https://devtron.ai/pricing)
diff --git a/docs/user-guide/global-configurations/container-registries.md b/docs/user-guide/global-configurations/container-registries.md
index 846eea8e8..12c6cf423 100644
--- a/docs/user-guide/global-configurations/container-registries.md
+++ b/docs/user-guide/global-configurations/container-registries.md
@@ -2,57 +2,70 @@
## Introduction
-While [container registries](../../reference/glossary.md#container-registry) are typically used for storing [images](../../reference/glossary.md#image) built by the CI Pipeline, an OCI registry can store container images as well as other artifacts such as [helm charts](../../reference/glossary.md#helm-charts-packages). In other words, all container registries are OCI registries, but not all OCI registries are container registries.
+A [Container Registry](../../reference/glossary.md#container-registry) acts as a storage place for container [images](../../reference/glossary.md#image) whereas an OCI Registry acts as a storage place for container images, [Helm charts](../../reference/glossary.md#helm-charts-packages), as well as other OCI-compliant artifacts.
-You can configure a container registry using any registry provider of your choice. It allows you to build, deploy, and manage your container images or charts with easy-to-use UI.
+You can pull Helm charts from either a public registry or a private registry (only if the registry contains Helm charts) and display them on the [Chart Store](../deploy-chart/README.md) page in Devtron.
+
+
+
+{% hint style="warning" %}
+
+### Who Can Perform This Action?
+
+Only a Super-Admin can create, update, or delete a container/OCI registry.
+
+{% endhint %}
---
-## Add Container Registry
+## Add an OCI Registry
### Steps
-1. From the left sidebar, go to **Global Configurations** → **Container/OCI Registry**.
+To add a container/OCI registry, follow the steps below:
- 
+1. Navigate to **Global Configurations** → **Container/OCI Registry**.
+
+ 
2. Click **Add Registry**.
- 
+ 
-3. Choose a provider from the **Registry provider** dropdown. View the [Supported Registry Providers](#supported-registry-providers).
+3. Choose your preferred registry provider from the **Registry provider** drop-down box. Refer to [Supported Registry Providers](#supported-registry-providers) for more information.
4. Choose the Registry type:
- * **Private Registry**: Choose this if your images or artifacts are hosted or should be hosted on a private registry restricted to authenticated users of that registry. Selecting this option requires you to enter your registry credentials (username and password/token).
- * **Public Registry**: Unlike private registry, this doesn't require your registry credentials. Only the registry URL and repository name(s) would suffice.
-5. Assuming your registry type is private, here are few of the common fields you can expect:
+ * **Private Registry**: Select this if your images or artifacts are hosted, or should be hosted, on a private registry restricted to the authenticated users. Selecting this option requires you to enter your registry credentials (username and password/token).
+
+ * **Public Registry**: Unlike private registry, this option does not require credentials. You only need to provide the registry URL and repository name(s).
+
+5. Refer to the following table and enter the required details:
| Fields | Description |
| --- | --- |
- | **Name** | Provide a name to your registry, this name will appear in the **Container Registry** drop-down list available within the [Build Configuration](../creating-application/docker-build-configuration.md) section of your application|
- | **Registry URL** | Provide the URL of your registry in case it doesn't come prefilled (do not include `oci://`, `http://`, or `/https://` in the URL) |
- | **Authentication Type** | The credential input fields may differ depending on the registry provider, check [Registry Providers](#supported-registry-providers) |
- | **Push container images** | Tick this checkbox if you wish to use the repository to push container images. This comes selected by default and you may untick it if you don't intend to push container images after a CI build. If you wish to to use the same repository to pull container images too, read [Registry Credential Access](#registry-credential-access). |
- | **Push helm packages** | Tick this checkbox if you wish to [push helm charts to your OCI registry](#push-helm-packages) |
- | **Use as chart repository** | Tick this checkbox if you want Devtron to [pull helm charts from your registry and display them on chart store](#use-as-chart-repository). Also, you will have to provide a list of repositories (present within your registry) for Devtron to successfully pull the helm charts. |
- | **Set as default registry** | Tick this checkbox to set your registry as the default registry hub for your images or artifacts |
+ | **Name** | Enter your registry name. You can [find the username](https://devtron-public-asset.s3.us-east-2.amazonaws.com/images/use-cases/oci-pull/find-username.jpg) from your registry provider account. This name will also appear in the **Container Registry** drop-down box available within the [Build Configuration](../creating-application/docker-build-configuration.md) section of your application|
+ | **Registry URL** | Enter your registry URL (**Note**: do not include `oci://`, `http://`, or `/https://` in the URL) |
+ | **Authentication Type** | Select your preferred authentication type. The credential input fields may differ depending on the registry provider, check [Registry Providers](#supported-registry-providers)|
+ |**Connection Method** | * `Direct`: Select this option to directly connect to an API server that is on the same network or publicly accessible.
* `via Proxy`: Select this option to connect to a remote server that is behind a proxy and not directly reachable.
* `via SSH Tunnel`: Select this option to connect to a server that is not publically accessible, using a secure SSH connection|
+ | **Push container images** | Enable this checkbox if you'd like to use the repository to push container images. This checkbox is enabled by default, and you may disable it if you don't intend to push container images after a CI build. If you wish to to use the same repository to pull container images as well, read [Registry Credential Access](#registry-credential-access) |
+ | **Push helm packages** | Enable this checkbox if you wish to [push Helm charts to your OCI registry](#push-helm-packages) |
+ | **Use as chart repository** | Enable this checkbox if you want Devtron to [pull Helm charts from your registry and display them on Chart Store](#use-as-chart-repository). Also, you will have to provide a list of repositories (present within your registry) for Devtron to successfully pull the Helm charts |
+ | **Set as default registry** | Enable this checkbox to set your registry as the default registry hub for your images or artifacts |
6. Click **Save**.
### Push Helm Packages
-Upon enabling this option, Devtron supports the pushing of helm charts to your OCI registry.
-
-This is possible through [isolated clusters](../global-configurations/cluster-and-environments.md#add-isolated-cluster) that facilitate airgapped deployments. In other words, it generates a helm package that you can use to deploy your application in air-gapped clusters.
+Upon enabling this option, Devtron supports the pushing of Helm charts to your OCI registry.
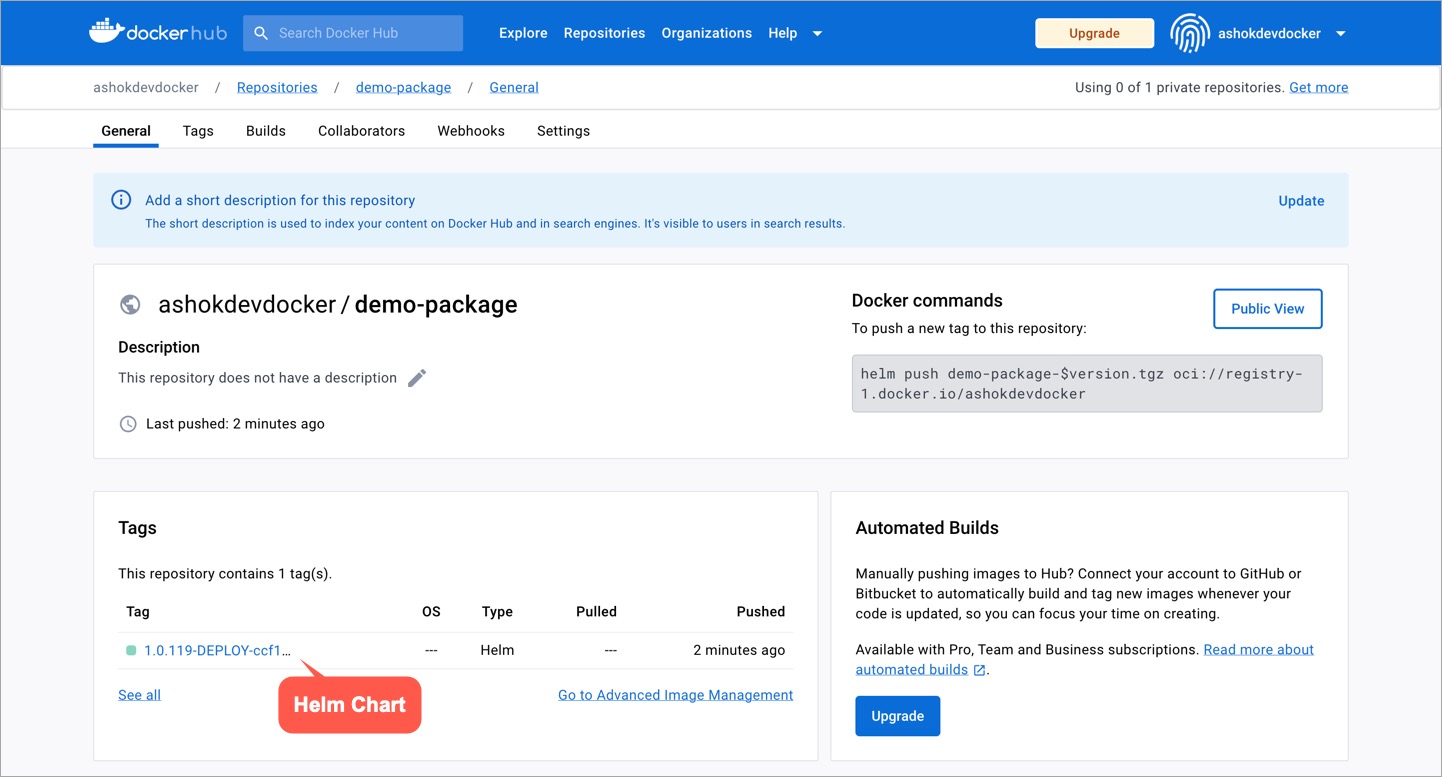
-If you have [configured your CD pipeline](../creating-application/workflow/cd-pipeline.md#deploying-to-an-isolated-environment) to push the helm package to your OCI registry, you can view the pushed helm package in your registry as shown below:
+This is possible through [isolated clusters](../global-configurations/cluster-and-environments.md#add-isolated-cluster) that facilitate airgapped deployments. In other words, it generates a Helm package that you can use to deploy your application in air-gapped clusters.
-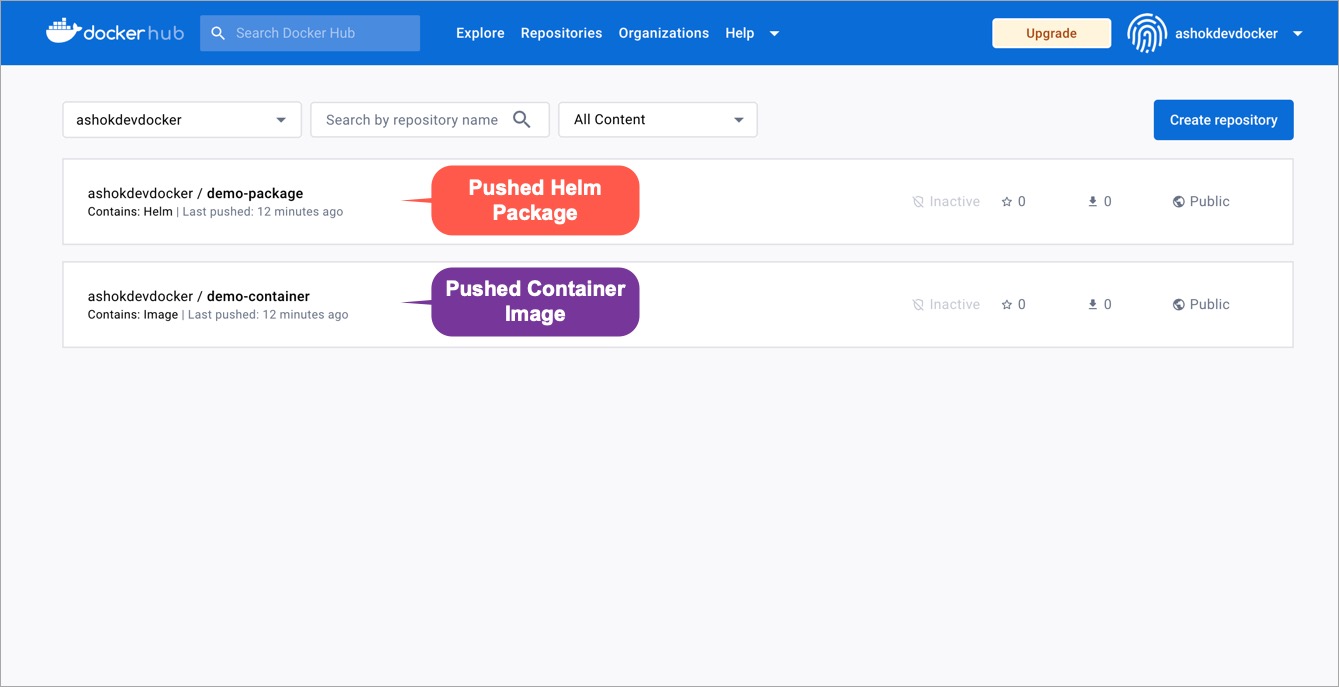
+If you have [configured your CD pipeline](../creating-application/workflow/cd-pipeline.md#deploying-to-an-isolated-environment) to push the Helm package to your OCI registry, you can view the pushed Helm package in your registry as shown below:
-
+
-{% hint style="warning" %}
+
### Use as Chart Repository
@@ -60,13 +73,11 @@ If you have [configured your CD pipeline](../creating-application/workflow/cd-pi
### Prerequisite
-OCI registry with `Use as chart repository` option enabled.
+An OCI registry containing Helm charts is added to the Container/OCI Registry page.
{% endhint %}
-Unlike Helm repos, OCI registries do not have an index file to discover all the charts. If you have helm packages pushed to your OCI registry, you can that registry as a chart repository.
-
-Upon enabling this option, Devtron can use your OCI registry as the chart source and pull the helm charts to display them on your [Chart Store](../deploy-chart/README.md) for easy deployment.
+When you have your own Helm charts in a private registry and prefer to use them, enable the **Use as chart repository** checkbox. The OCI registry is then considered as a chart repository, and all the existing charts are fetched and displayed in the [Chart Store](../deploy-chart/README.md).
#### Tutorial
@@ -74,11 +85,122 @@ Upon enabling this option, Devtron can use your OCI registry as the chart source
#### Steps
-Search your OCI registry in the list and click it.
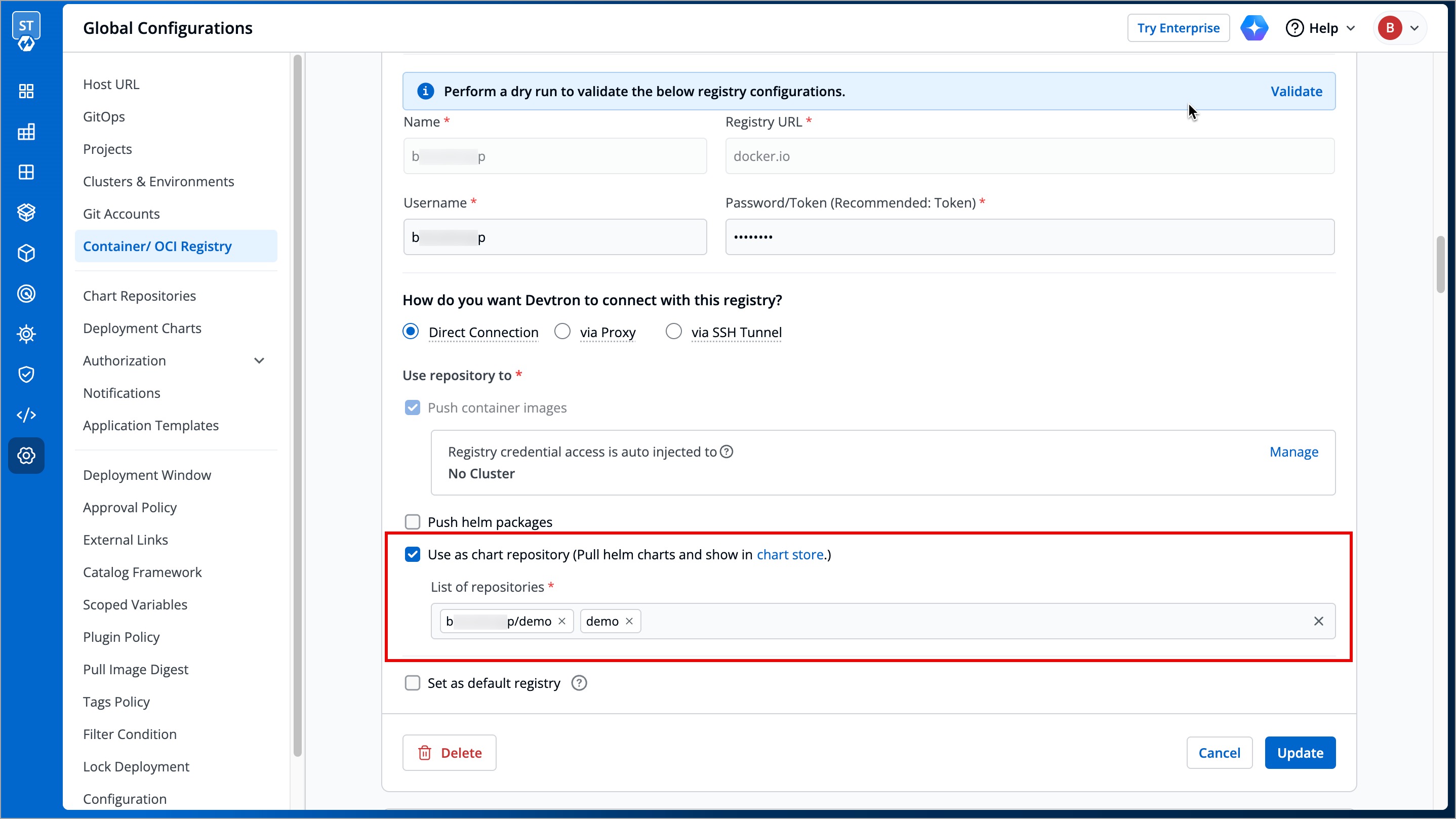
+To use an OCI registry as a chart repository, follow the steps below:
+
+1. Navigate to **Global Configurations** → **Container/OCI Registry**.
+
+2. Search for your preferred OCI registry in the list and select it.
+
+3. Add your chart repositories (where the helm charts are present) in the **List of repositories** field.
+
+ 
+
+4. Click **Save**.
+
+---
+
+## Registry Credential Access
+
+You can pull [images](../../reference/glossary.md#image) from a container/OCI registry, but when using private registries, it is important to control which clusters have acccess to pull the images. That is why managing registry credential access becomes crucial.
+
+You can choose to either auto-inject registry credentials to clusters or use a [Secret](../../reference/glossary.md#secrets) to pull an image for deployment to environments on specific clusters. When you choose to auto-inject registry credentials, the right authentication details (e.g., `username`/`password or token`) are automatically provided to a pod without the need of manual intervention.
+
+You can create a pod that uses a [Secret](../../reference/glossary.md#secrets) to pull an image from a private container registry of your choice (e.g., [Docker Hub](https://www.docker.com/products/docker-hub)).
+
+To manage the registry credential access, follow the steps below:
+
+1. Navigate back to the **Container/OCI Registry** page.
+
+2. Select your preferred registry.
+
+3. Click the **Manage** button displayed next to the **Registry credential access is auto injected to** label.
+
+ 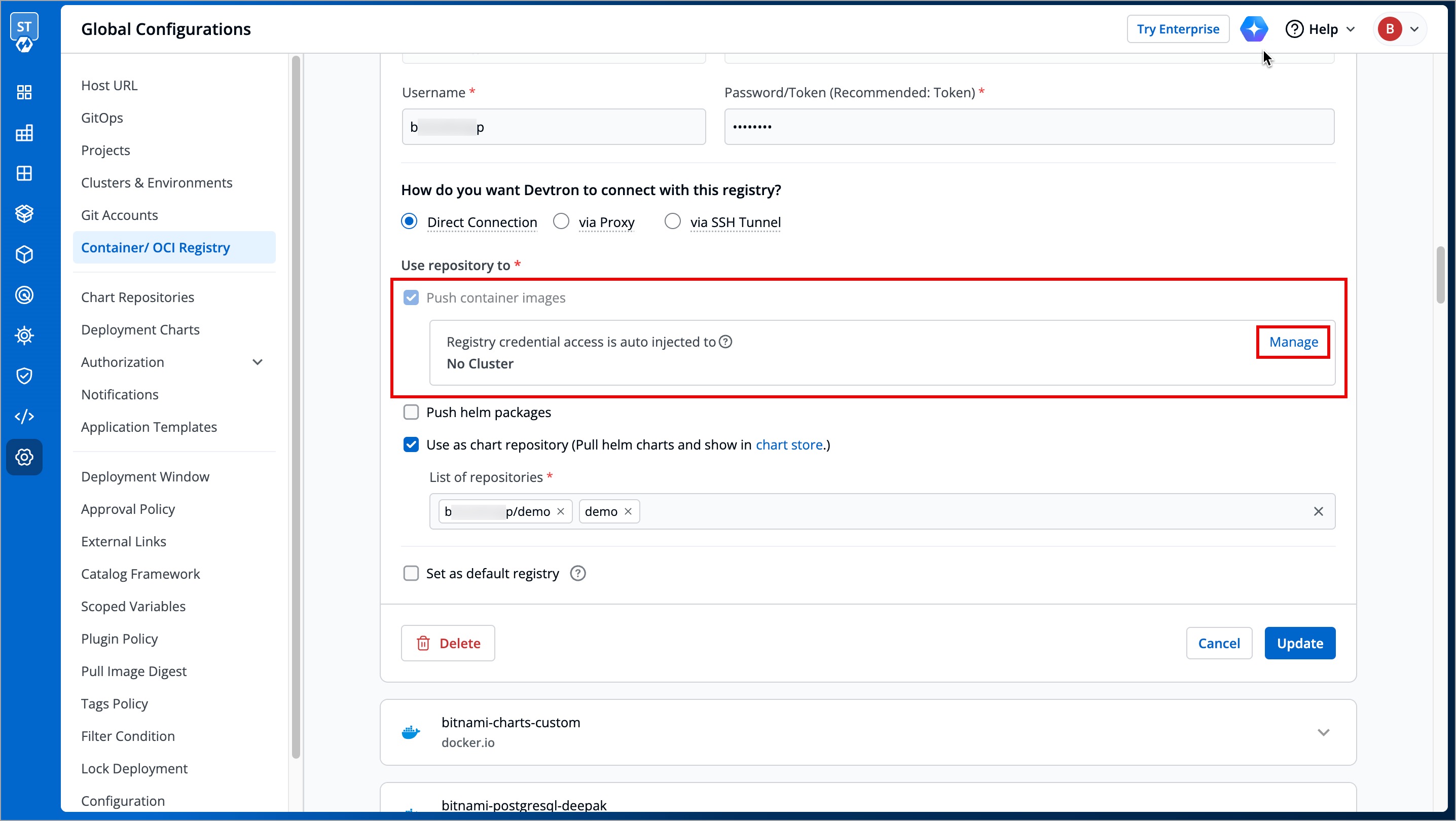
+
+ You can manage registry credential access in the following two ways:
+
+ | Fields | Description |
+ | --- | --- |
+ | **Do not inject credentials to clusters** | Select the clusters where you do not want to inject credentials |
+ | **Auto-inject credentials to clusters** | Select the clusters where you want to inject credentials |
+
+4. You can choose one of the two options for defining credentials:
+
+ * [Use Registry Credentials](#use-registry-credentials)
+
+ * [Specify Image Pull Secret](#specify-image-pull-secret)
+
+ 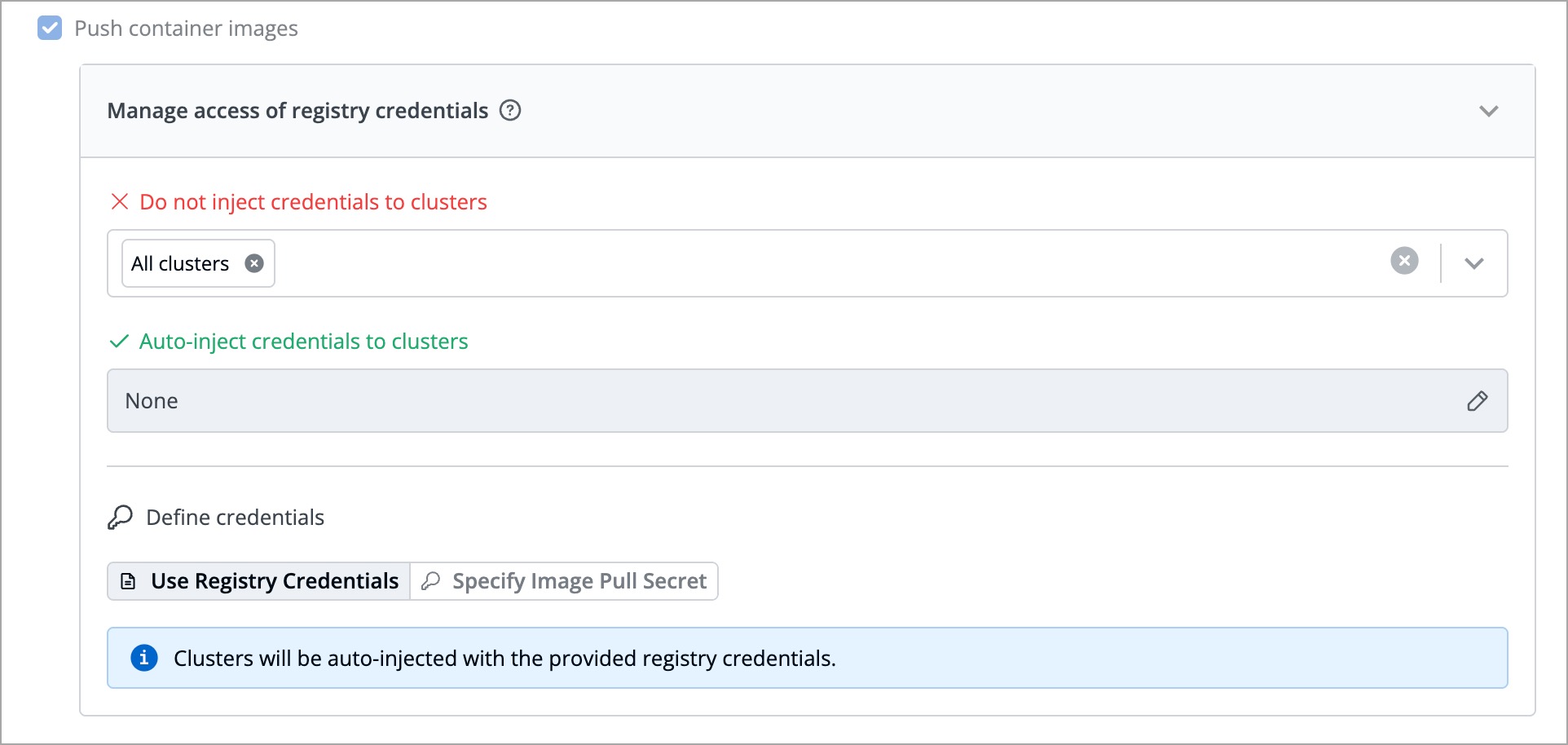
+
+5. Click **Save**.
+
+### Use Registry Credentials
+
+If you select **Use Registry Credentials**, the clusters will be auto-injected with the registry credentials of your registry type. As an example, if you select **Docker** as the registry type, then the clusters will be auto-injected with the `username` and `password/token` associated with your Docker Hub account.
+
+
+
+### Specify Image Pull Secret
+
+You can create a Secret by providing credentials on the Command Line/Terminal.
+
+
+
+1. Navigate back to the **Container/OCI Registry** page.
+
+2. Enter the secret name (e.g., `regcred`) in the **Specify Image Pull Secret** section.
+
+3. Refer to the table below and enter the following command in the Command Line/Terminal to create a Secret:
+
+{% hint style="info" %}
+
+### Important Note
-In the **List of repositories** field, add your chart repo(s). You can [find the username](https://devtron-public-asset.s3.us-east-2.amazonaws.com/images/use-cases/oci-pull/find-username.jpg) from your registry provider account.
+Docker is used just as an example here. However, you can create Secrets with any registry provider of your choice.
+{% endhint %}
+```bash
+kubectl create -n secret docker-registry regcred --docker-server= --docker-username= --docker-password= --docker-email=
+```
+
+| Key | Description |
+| --- | --- |
+| `namespace` | Specify your sub-cluster (e.g., **devtron-demo**) |
+| `your-registry-server` | Specify your private Docker registry FQDN. For Docker Hub, use https://index.docker.io/v1/ |
+| `your-name` | Specify your Docker registry username (e.g., `johndoe`) |
+| `your-pword` | Specify your Docker password |
+| `your-email` | Specify your Docker email id |
+
+You have successfully set your Docker credentials in the cluster as a Secret called `regcred`.
+
+{% hint style="warning" %}
+
+When you enter Secrets in the Command Line/Terminal while `kubectl` is running, the Secrets can get stored in your shell history unprotected, and can also be temporarily visible to other users.
+
+{% endhint %}
+
+## Delete an OCI Registry
+
+If you prefer to delete an OCI registry, follow the instructions below:
+
+1. Navigate back to **Container/OCI Registry** page.
+
+ 
+
+2. Select your preferred OCI registry.
+
+3. Click the **Delete** button. The OCI registry will be deleted.
+
+{% hint style="warning" %}
+
+### Important Note
+
+If you used an OCI registry as a chart source, deleting the OCI registry will remove all its associated charts from the Chart Store.
+
+{% endhint %}
+
+---
## Supported Registry Providers
@@ -166,83 +288,7 @@ Provide below information if you select the registry type as `Other`.
| **Advanced Registry URL Connection Options** | - **Allow Only Secure Connection**: Tick this option for the registry to allow only secure connections
- **Allow Secure Connection With CA Certificate**: Tick this option for the registry to allow secure connection by providing a private CA certificate (ca.crt)
- **Allow Insecure Connection**: Tick this option to make an insecure communication with the registry (for e.g., when SSL certificate is expired)
|
{% hint style="info" %}
-You can use any registry which can be authenticated using `docker login -u -p `. However these registries might provide a more secured way for authentication, which we will support later.
-{% endhint %}
-
-
-## Registry Credential Access
-
-You can create a Pod that uses a [Secret](../../reference/glossary.md#secrets) to pull an image from a private container registry. You can use any private container registry of your choice, for e.g., [Docker Hub](https://www.docker.com/products/docker-hub).
-
-Super-admin users can decide if they want to auto-inject registry credentials or use a secret to pull an image for deployment to environments on specific clusters.
-
-1. To manage the access of registry credentials, click **Manage**.
-
-There are two options to manage the access of registry credentials:
-
-| Fields | Description |
-| --- | --- |
-| **Do not inject credentials to clusters** | Select the clusters for which you do not want to inject credentials |
-| **Auto-inject credentials to clusters** | Select the clusters for which you want to inject credentials |
-
-2. You can choose one of the two options for defining credentials:
-
-* [Use Registry Credentials](#use-registry-credentials)
-* [Specify Image Pull Secret](#specify-image-pull-secret)
-
-### Use Registry Credentials
-
-If you select **Use Registry Credentials**, the clusters will be auto-injected with the registry credentials of your registry type. As an example, If you select `Docker` as Registry Type, then the clusters will be auto-injected with the `username` and `password/token` which you use on the Docker Hub account.
-
-Click **Save**.
-
-
-
-### Specify Image Pull Secret
-
-You can create a Secret by providing credentials on the command line.
-
-
-
-Create this Secret and name it `regcred` (let's say):
-
-```bash
-kubectl create -n secret docker-registry regcred --docker-server= --docker-username= --docker-password= --docker-email=
-```
-
-where,
-
-* **namespace** is your sub-cluster, e.g., devtron-demo
-* **your-registry-server** is your Private Docker Registry FQDN. Use https://index.docker.io/v1/ for Docker Hub.
-* **your-name** is your Docker username
-* **your-pword** is your Docker password
-* **your-email** is your Docker email
-
-You have successfully set your Docker credentials in the cluster as a Secret called `regcred`.
-
-{% hint style="warning" %}
-Typing secrets on the command line may store them in your shell history unprotected, and those secrets might also be visible to other users on your PC during the time when kubectl is running.
-{% endhint %}
-
-Enter the Secret name in the field and click **Save**.
-
-## Delete an OCI Registry
-
-If you prefer to delete an OCI registry, follow the instructions below:
-
-1. Navigate back to **Container/OCI Registry** page.
-
- 
-
-2. Select your preferred OCI registry.
-
-3. Click the **Delete** button. The OCI registry will be deleted.
-
- {% hint style="warning" %}
-
- ### Important Note
-
- If you used an OCI registry as a chart source, deleting the OCI registry will remove all its associated charts from the Chart Store.
+You can use any registry which can be authenticated using `docker login -u -p `. However these registries might provide a more secured way for authentication, which we will support later.
- {% endhint %}
\ No newline at end of file
+{% endhint %}
\ No newline at end of file
diff --git a/docs/user-guide/plugins/copy-container-image.md b/docs/user-guide/plugins/copy-container-image.md
index 6e6f59080..fb677b24a 100644
--- a/docs/user-guide/plugins/copy-container-image.md
+++ b/docs/user-guide/plugins/copy-container-image.md
@@ -28,7 +28,7 @@ The plugin can be used at post CI, pre-CD, and post-CD. Moreover, you can also [
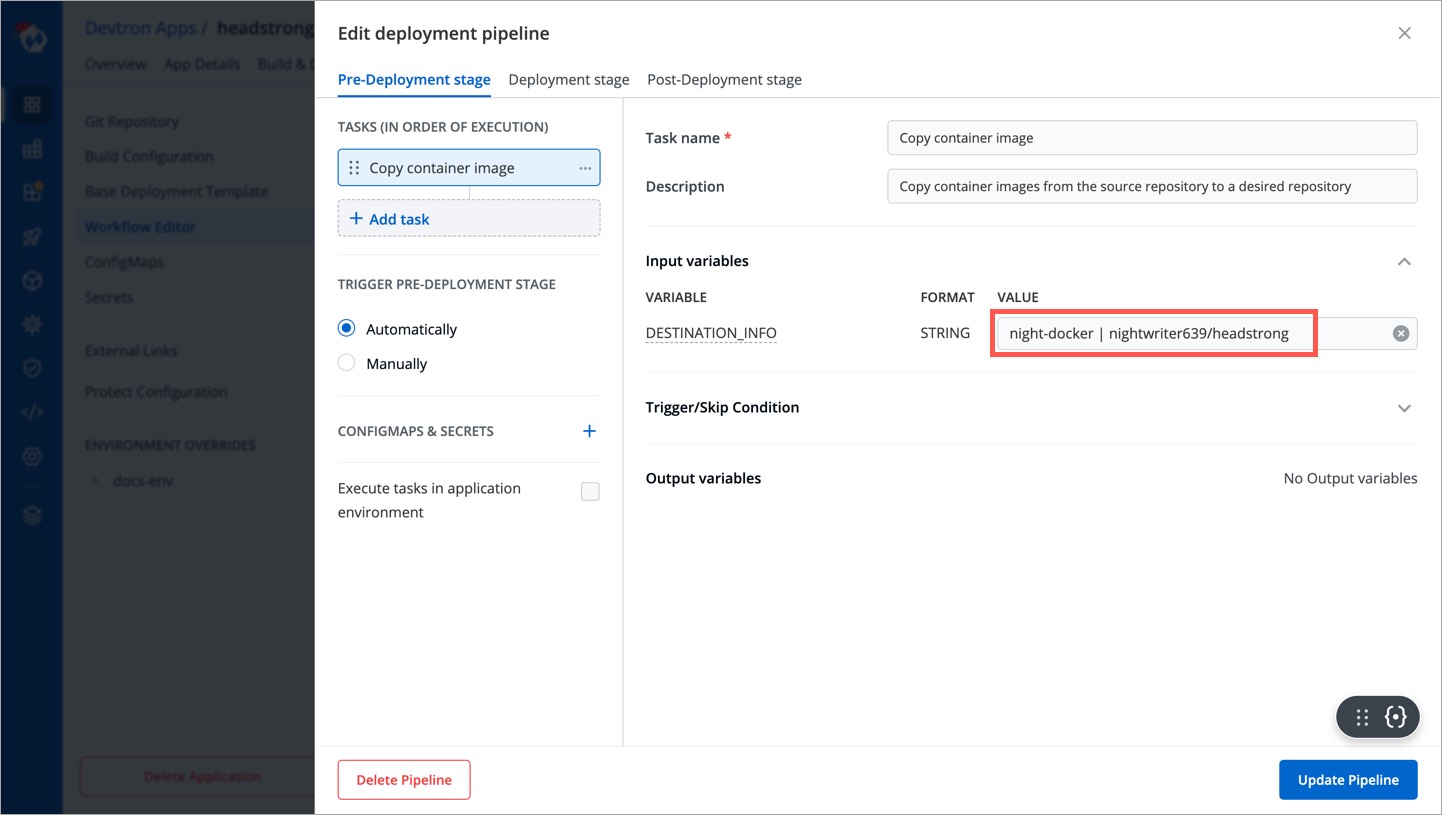
- * **registry-name** is the name you gave to your container registry while adding it in [Global Configuration → OCI/Container Registry](../global-configurations/container-registries.md#add-container-registry).
+ * **registry-name** is the name you gave to your container registry while adding it in [Global Configuration → OCI/Container Registry](../global-configurations/container-registries.md#add-an-oci-registry).
* **user-name** is the your account name registered with you container registry, e.g., DockerHub.
diff --git a/docs/user-guide/use-cases/README.md b/docs/user-guide/use-cases/README.md
index e0bdab866..2377959c3 100644
--- a/docs/user-guide/use-cases/README.md
+++ b/docs/user-guide/use-cases/README.md
@@ -11,3 +11,5 @@ In this comprehensive guide, you will find a wide range of use cases, illustrati
[Connect Expressjs With Mongodb Database](connect-expressjs-with-mongodb-database.md)
[Connect Django With Mysql Database](connect-django-with-mysql-database.md)
+
+[Deploying Software on Air-gapped Environment](airgapped-app-deployment.md)
\ No newline at end of file
diff --git a/docs/user-guide/use-cases/airgapped-app-deployment.md b/docs/user-guide/use-cases/airgapped-app-deployment.md
new file mode 100644
index 000000000..c8917464b
--- /dev/null
+++ b/docs/user-guide/use-cases/airgapped-app-deployment.md
@@ -0,0 +1,39 @@
+# Deploying Software to Air-Gapped Environments with Devtron
+
+## Problem Statement
+
+Industries such as healthcare, banking, and finance, have regulations that require certain data to be stored and processed in air-gapped environments. Air-gapped environments are more secure and since they are not exposed to the public, they are less vulnerable to attacks. However, this isolation brings challenges when it comes to receiving and deploying software updates, security patches, bug fixes which generally depend on Internet availability.
+
+Devtron ensures reliable delivery of software updates regardless of whether your air-gapped environment has Internet access or not. By using Devtron’s OCI push/pull features and helm package generation, vendors and clients can overcome the challenges posed by air-gapped environments
+
+---
+
+## How Devtron Helps Solve the Problem:
+
+### Scenario 1: Air-Gapped Cluster has access to OCI registry
+
+In cases where the air-gapped cluster gets controlled access to the Internet, Devtron's OCI push/pull feature helps in delivering your software via OCI registry.
+
+1. **Vendor Action:**
+
+ - The vendor uses Devtron to generate and [push Helm package](../global-configurations/container-registries.md#push-helm-packages) to an OCI registry (accessible to both vendor and client) by deploying to an [isolated cluster](../creating-application/workflow/cd-pipeline.md#deploying-to-an-isolated-environment).
+
+2. **Client Action:**
+ - The client can install the helm package from the OCI registry using their existing deployment tools, or use Devtron to [pull the Helm package](../global-configurations/container-registries.md#use-as-chart-repository) from the OCI registry to their [Chart Store](../deploy-chart/README.md).
+ - Once the Helm package is pulled, it [appears in the Chart Store](../deploy-chart/README.md#fetch-and-populate-charts), allowing easy deployment to the air-gapped environment.
+
+
+### Scenario 2: Air-Gapped Cluster has no Internet Access
+
+In fully air-gapped environments with no Internet access, the vendor and client may rely on physical transfer of Helm packages. Devtron facilitates this as follows:
+
+1. **Vendor Action:**
+ - Similar to [Scanario 1](#scenario-1-air-gapped-cluster-has-access-to-oci-registry), the vendor generates a helm package by deploying the application to an [isolated cluster](../global-configurations/cluster-and-environments.md#add-isolated-cluster).
+ - Since the client has no access to the Internet, the vendor need not push it to the OCI registry but rather download the generated Helm package either from [App Details](https://devtron-public-asset.s3.us-east-2.amazonaws.com/images/use-cases/oci-push/app-details-page.jpg) or [Deployment History](https://devtron-public-asset.s3.us-east-2.amazonaws.com/images/use-cases/oci-push/deployment-history-page.jpg) page of the app in Devtron.
+ - The Helm package (available in .tgz format) is handed over by the vendor to the client via a portable storage device (e.g., USB drive).
+
+2. **Client Action:**
+ - The client manually uploads the Helm package to their air-gapped cluster by mounting the storage device.
+ - The client deploys the package to the environment using their deployment tools, CLI, or [Cluster Terminal in Devtron's Resource Browser](../resource-browser/cluster-terminal.md).
+
+This method ensures that clients using air-gapped clusters, even without Internet access, can securely receive software updates.
\ No newline at end of file
diff --git a/docs/user-guide/use-cases/oci-pull.md b/docs/user-guide/use-cases/oci-pull.md
deleted file mode 100644
index d62cc0a75..000000000
--- a/docs/user-guide/use-cases/oci-pull.md
+++ /dev/null
@@ -1,73 +0,0 @@
-# Pull Helm Charts from OCI Registry
-
-## Introduction
-
-Devtron supports the installation of [Helm charts](../../reference/glossary.md#helm-chartspackages) from both: Helm [repos](../../reference/glossary.md#repo) and [Container/OCI registries](../../reference/glossary.md#containeroci-registry). Unlike Helm repos, OCI registries do not have an index file to discover all the charts. However, Devtron makes it easier for you to populate your charts from multiple sources to the [chart store](../../reference/glossary.md#chart-store).
-
-**Prerequisites**
-
-* Helm Chart(s)
-* OCI-compliant Registry (e.g. Docker Hub and [many more](../global-configurations/container-registries.md#supported-registry-providers))
-
-You must [add your OCI registry](../global-configurations/container-registries.md) to Devtron with the `Use as chart repository` option enabled.
-
----
-
-## Tutorial
-
-{% embed url="https://www.youtube.com/watch?v=9imC5MMz9gs" caption="Pulling Charts from an OCI Registry to Devtron" %}
-
----
-
-## Populating your Charts to the Chart Store
-
-1. Go to **Global Configurations** → **Container/OCI Registry**.
-
-2. Search your OCI registry in the list, and click it.
-
-3. In the **List of repositories**, add the chart repo(s). The format should be `username/chartname`. You can find the username from your registry provider account.
-
- 
-
-4. Click **Save** or **Update**.
-
-5. From the left sidebar, go to **Chart Store**.
-
-6. You can find your chart(s) either by using the search bar or by selecting your chart source.
-
- 
-
-You have successfully pulled your charts to the chart store.
-
-
-
-### Unable to find your Charts?
-
-Deprecated charts won't show up in the Chart Store unless you enable the **Show deprecated charts** filter as shown below
-
-
-
-Or, you may try performing a resync as shown below
-
-
-
----
-
-
-## Removing your Chart from the Chart Store
-
-1. Go to your OCI registry settings in Devtron.
-
-2. In the **List of repositories** field, remove the unwanted chart repo.
-
- 
-
-3. Click **Update**.
-
-The removed chart would no longer appear in the Chart Store.
-
-{% hint style="info" %}
-Deleting a chart repo from your OCI registry will not lead to the removal of chart from the Chart Store
-{% endhint %}
-
-