-
Notifications
You must be signed in to change notification settings - Fork 67
4. SHAREM’s Disassembler
SHAREM can also generate other useful data about a sample. From the main menu, the D option can be used to generate annotated disassembly of a shellcode file. This optional allows the user to easily look through the code and identify where significant malicious actions occur, such as PEB walking sequences.
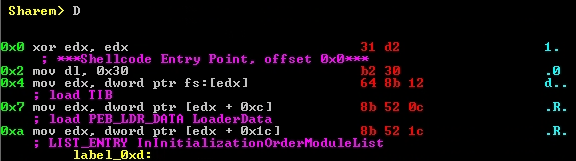
Options regarding the disassembly feature can be found in option accessible by typing d at the main menu.
The disassembly engine is done with several custom analysis functions, and it is done through static analysis. It is significantly more accurate at analyzing shellcode than all other disassemblers. However, it is recommended to run the disassembler only after having emulated the shellcode. The reason why is that API’s that are identified can then be identified in the disassembly. Additionally, SHAREM will combine the results of the emulation to improve the static analysis. When the emulation is run with code coverage, the results can be nearly flawless. Note that when emulated, the results of emulation are prioritized and “override” any differences (if any) from static analysis, but it is done byte by byte.
If shellcode was encoded but has been deobfuscated, the disassembler by default will show the deobfuscated shellcode, rather than the encoded bytes – which are meaningless to the user.
The disassembler provides rich, aesthetically pleasing coloring for different elements of the disassembly. It also saves the disassembly as a text file, and as a JSON file. The JSON file can be imported into a web site, as can all the results.