-
Notifications
You must be signed in to change notification settings - Fork 68
8. Modules and Imports in PE Files
HAREM can detect imported modules and functions inside PE files. While the q and z options automatically execute each of these features, they can all be individually executed and tweaked as well using their corresponding menu options. These options can also be selected and executed via the internal menus.
The m option at the main menu allows the user to find modules loaded by the sample. The user is presented with a submenu:
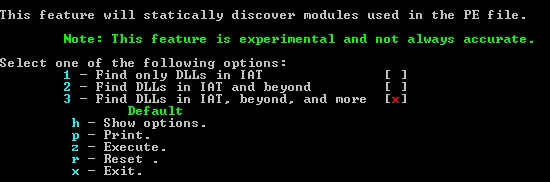
Option 1 only looks for modules in the IAT of the sample. The other options search deeper, looking for modules loaded by other modules. This feature allows the user to find all modules effectively loaded by the PE file, even if they are not loaded directly by the sample itself. When selecting #3, the options are often set according to InOrderModuleList, although these are found recursively with our custom function. It does seem that the order in this can vary slightly depending on the OS and release and unique settings, so there may not necessarily be a definitive InOrderModuleList for something that has numerous DLLs, as variation can exist. Another unique feature is that it will tell where the module came from – for instance, did it come from the IAT or another DLL’s IAT? We are not aware of another tool with that feature.
Similarly, typing e at the main menu brings the user to a submenu where they can print functions imported by the sample. As with many of the other submenus, the z command executes the functionality, and discovered imports can be reset with r. Unusual imports could indicate malicious activity in a sample – for example, imports for networking capabilities in a simple video player may be worth investigating.